Blog
21 April, 2024
January 11, 2024
The Kubernetes Adoption Framework (KAF) methodology introduces a dedicated solution concept for adopting Kubernetes technology in any organization. This concept encompasses the construction of all processes and integrations designed for the organization’s Kubernetes environments. It was developed by TeraSky after completing numerous projects and gaining a deep understanding of the pains and challenges organizations face. This is the main reason for the creation of KAF. The methodology is modular and can be readily customized to align with the complexity and maturity level of organizations adopting Kubernetes. It streamlines the process and comprehensively maps and outlines the various challenges organizations may encounter at different stages of the implementation process.
Organizations face several similar challenges when adopting Kubernetes. One major pain point is the inherent complexity of implementing and managing Kubernetes, requiring specialized knowledge and careful setup. A potential skills gap adds to the difficulty, as finding professionals well-versed in Kubernetes can be challenging. The operational overhead is significant, demanding ongoing maintenance, monitoring, and troubleshooting resources. Security concerns are paramount, with misconfigurations posing risks to the organization. Integration with existing infrastructure and applications presents another challenge, especially in legacy systems. Efficient resource utilization and scaling demand meticulous planning to avoid wasteful overprovisioning or underutilization. A cultural shift towards DevOps practices is often necessary, requiring collaboration and a change in mindset regarding application deployment and management. Cost management, including infrastructure, tools, and skilled personnel, is a continuous concern. Keeping Kubernetes and associated components up to date while ensuring compatibility with existing applications is a delicate balancing act. Finally, achieving comprehensive visibility into the Kubernetes environment and effectively monitoring performance adds to the ongoing challenges organizations encounter.
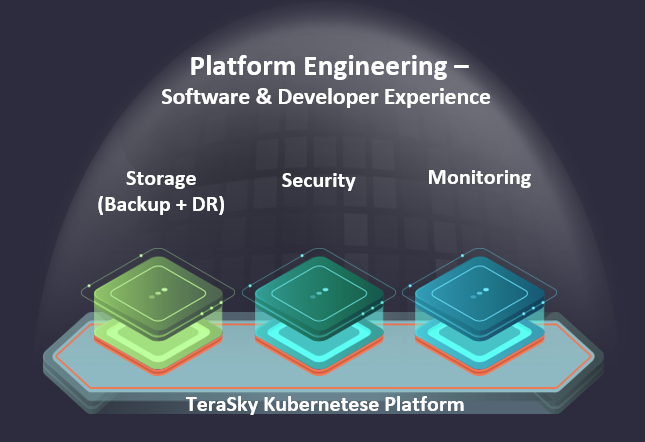
When we talk about Kubernetes, we usually only refer to the first building block, which is the basic and fundamental Infrastructure Layer enabling the existence of the environment. When organizations want to move one step further and run different applications and services in a production environment, they must address important aspects such as providing solutions for their storage, data backup, and disaster recovery. Another example is defining the performance target of their storage. These subjects are part of the second building block of the framework: Storage.
The third building block, Security, requires organizations to safeguard their environment against numerous vulnerabilities. Given the rapid changes in the environment, what held true yesterday may no longer apply, requiring us to promptly and continuously address vulnerabilities.
The average lifespan of a container is just four hours, making traditional approaches like quarterly or monthly scans impractical. Immediate action and a shift-left approach across the entire development chain become necessary.
The fourth building block, Monitoring, enables comprehensive visibility and monitoring within the entire Kubernetes environment. Unlike the legacy environment, where an agent was installed on a host and registered to a central monitoring system, the dynamic nature of Kubernetes demands a different solution, one that takes into account the hundreds of nodes and pods constantly going up and down. Understanding the relationships between the different objects is crucial for getting a full view and insight into the Kubernetes environment.
These four building blocks form the foundation, serving developers by providing them with the tools and environment to focus on the main objective, which is development. This leads to the fifth and most important building block: Software & Developer Experience. If developers cannot leverage Kubernetes quickly, it directly impacts the services and products they provide to their organization and customers. The goal is to minimize dealing with infrastructure management daily and focus more on the development processes. The development processes include both third-party, open-source applications used on the platform and applications developed in-house within the environment.
These building blocks were written based on TeraSky’s observations and represent what most organizations typically implement and execute. We created workflows to address each building block and realize the benefits mentioned earlier. Each workflow represents a different building block and comprises a complete, separate process with detailed steps and deliverables. This method is modular, allowing the organization to choose to focus on a specific workflow or all of them based on their unique business needs and the maturity level of their Kubernetes adoption.
In most cases, due to various constraints like time, money, experience, and more, organizations cannot thoroughly consider and address all points. This leads to numerous assumptions and default configurations that may not necessarily align with their business and IT needs. The primary issue lies in the lack of post-implementation review and adjustment to align the environment with actual needs. Without anyone to assess, repair, or rebuild as necessary, organizations find themselves in an environment that doesn’t truly meet their requirements. Consequently, they may neglect or only partially utilize the environment, leading to critical issues that arise later and result in delays.
In the end, organizations are looking for true technology adoption for their organization.
To simplify the process, each workflow is divided into three parts. The first part involves a deep dive workshop, which is a physical session where collaboration with the customer occurs within the organization’s real environment, addressing design, definitions, etc. This allows us to ask the customer simple and targeted questions – such as worker node headroom or precise calculator of control plane resources – that we can later translate into actionable tasks.
The second part is the outcome of the workshop, providing the customer with a detailed Low-Level Design document containing the conclusions and action items necessary for implementation.
In the third part, the customer receives a production-ready environment built according to best practices, including certification, least privilege, sizing, and configuration. It’s important to note that this environment is a real production environment that is developed incrementally, progressing through various stages.
The entire process follows an agile methodology and is completed within a few weeks, delivering fast, tangible results and products to the customer. We aim to tailor this process to the rapid development occurring within the customer’s organization. All of these steps are taken collaboratively with the customer and their teams, allowing them to provide input and engage in thoughtful discussions throughout the entire process. This approach makes it much easier to implement the right changes and adjustments as needed. The goal is ultimately for the customer to take ownership of the environments and gain the necessary knowledge to manage the various aspects of their environment.
The TeraSky KAF has assisted many organizations at different stages in navigating the Kubernetes adoption process strategically and responsibly for the long term. Organizations using this methodology will ensure the security, durability, monitoring, cost-effectiveness, and easy maintainability of their Kubernetes environment.
Written by: Mor Lila, Sr. Sales Engineer