Blog
21 April, 2024
April 4, 2023
At TeraSky, we pride ourselves on finding ways to save our customers money while always providing top-notch service. Recently, I had the opportunity to work with a customer who was looking to reduce their monthly expenses. This customer had an unusual, significant expense associated with the AWS Key Management Service (KMS). After thoroughly analyzing their current usage, spending, and environment structure, I identified a key area where major savings could be achieved: the encryption key type.
The customer used KMS (SSE-KMS) to encrypt their data stored in S3. By recommending that they switch to S3-managed keys (SSE-S3), we achieved a 90% decrease in the customer’s monthly KMS expenses.
The main difference between the two encryption types is that KMS uses a customer-managed key (CMK) to encrypt the data, while S3-managed keys use a key that is managed by S3 and will only share an S3 Bucket Key for objects encrypted by the same AWS KMS key.
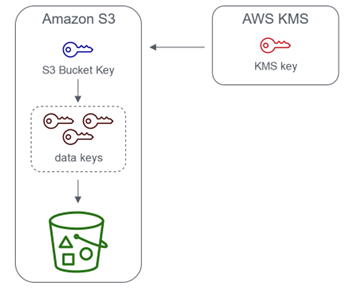
Server-side encryption with AWS Key Management Service using an S3 Bucket Key
The advantage of S3-managed keys is that the customer does not incur any additional charges for using the key.
This happens because KMS is a managed service that requires using a CMK for each encrypted object. This means the client was paying for using multiple CMKs, which added up quickly.
S3-managed keys, on the other hand, use a single key for the entire bucket. This eliminates the need for multiple CMKs, thus reducing the overall cost. Importantly, both encryption options provide the same level of security. The only difference is in the cost and management of the keys.
In addition to the savings, the customer also benefited from the added convenience of not having to manage their own encryption keys, freeing up valuable resources and allowing them to focus on other areas of their business.
The technical process and S3 cost
The technical process for switching from KMS to S3-managed keys is relatively straightforward.
First, we assessed the client’s current usage of KMS and identified the number of CMKs in use.
Next, we created a new S3-managed key and configured it for the client’s S3 bucket. This key can encrypt and decrypt all objects within that bucket, eliminating the need for multiple CMKs.
Then, we updated the client’s application or script to use the new S3-managed key for encryption and decryption instead of the previous KMS keys.
Finally, we tested the encryption and decryption process to ensure it was working correctly and the data was properly protected.
But what about the S3 cost?
S3 storage is generally cheaper than KMS, and S3-managed keys do not incur additional charges. However, if the client’s usage of S3 storage increases, then the cost of storing data on S3 will be higher. Even so, the cost of using the S3-managed key for encryption will be less than using multiple CMKs with KMS, ultimately leading to a lower overall cost.
Summary
Changing the encryption key type from KMS (SSE-KMS) to S3-managed keys (SSE-S3) not only saved our customer money but also provided them with a more convenient and secure way of encrypting their data stored in S3. We achieved significant cost savings by reviewing and optimizing their usage and spending on cloud services without compromising security or functionality.
Overall, this experience reinforced the importance of regularly reviewing and optimizing usage and spending on cloud services. By identifying and implementing simple changes, it is possible to achieve significant cost savings without compromising on security or functionality.
Cost

Before the change

After the change
Due to the change, the number of requests and the cost decreased by 92%.
Written by: Halit Levin, FinOps & Customer Success Manager