Blog
21 April, 2024
November 6, 2022
At TeraSky, our clients span the spectrum, from high-profile, global firms to smaller startups to governmental agencies. No matter their field or area of expertise, they all need better network security. While all other aspects of the technology industry, like storage and virtualization, have become virtual, the network itself has been “left behind,” so to speak. NSX-T, a software-defined network product, is VMware’s solution to this problem, and in the time that I’ve been in my current role, it has become one of my favorite tools to work with.
NSX-T provides micro-segmentation, a method of establishing “zones” in data centers and cloud environments to isolate workloads from one another. Doing so means that NSX-T can achieve things that firewalls can’t. For example: if there are two VMs that are located on the same network, a firewall cannot block any communication between them. NSX-T’s micro-segmentation makes it possible to deny all traffic or specific services, even between VMs on the same network.
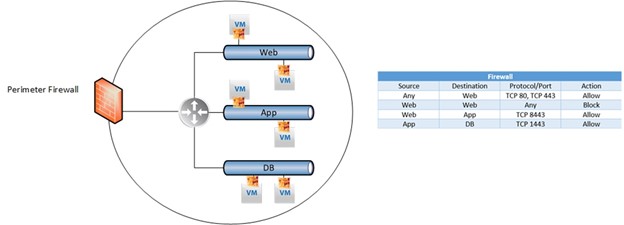
One of the major challenges that clients face when approaching a project like micro-segmentation is that they are often not perfectly familiar with the entirety of their environment. For this reason, NSX-T works cooperatively with vRNI. vRNI (vRealize Network Insight) gets added to vCenter (where the VMs are) and essentially maps out the environment: which VMs communicate with which other VMs? What kind of communication is taking place, and how often? Once this mapping is completed, we export the vRNI firewall rules recommendations; the client then reviews this policy list and removes communication connections that are not relevant..
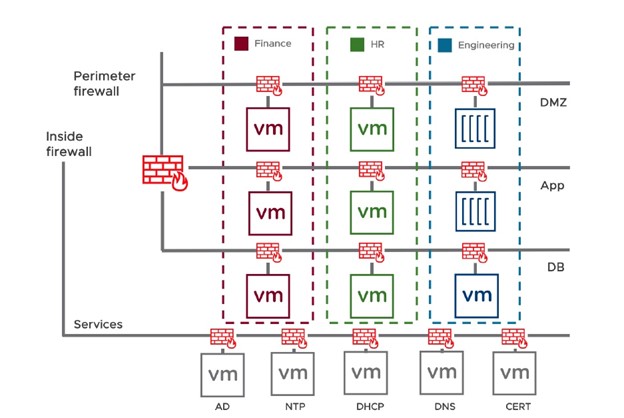
One recent project provides an example of a great NSX-T use case. A significant global clothing supplier hired us for a two-phased project. Phase 1 was to complete east-west micro-segmentation for their data center, which included about 400 or 500 machines. Over the course of seven months, we met with the client every two weeks to establish the policy definitions for NSX-T, using vRNI to map the environment. As we worked, we also employed vRLI (vRealize Log Insight) to identify violations to the proposed policy within the environment based on the rule ID – something that is otherwise difficult to pinpoint accurately and which is simplified significantly by vRLI’s ordered verification approach and violation logging.
Once we felt as confident as possible in our policy whitelist, we finished it by changing the last rule to any-any-deny (throughout the project, it was any-any-allow). We started first thing in the morning and stayed at the client’s offices throughout the day in order to be immediately available in case any elements were mistakenly excluded (I am happy to add that none were).
After working smoothly and successfully with the resulting policy for about six months, the client asked to move forward with Phase 2, which was a north-south micro-segmentation. They wanted to prevent their global external sites from accessing their data center, where they store all of their applications, accounts, and more. For NSX-T to operate its features on any given environment, it must be installed on that environment. Because NSX-T was installed only on the client’s data center and not on all of the sites around the world, the client’s deep organizational knowledge and familiarity with their environment was invaluable. Based on the IP range, which identifies the site location worldwide, the client could determine which policies should be applied to which sites. We then used NSX-T to establish corresponding security groups, allowing only approved entities to communicate with the data center.
Another strategy that saved a lot of time and reduced the project’s complexity was to apply DFW automation to all of the repetitive tasks – particularly when faced with 300, 500, or even 1000 VMs that all need to be tagged. Doing it manually would take weeks to accomplish. By applying DFW automation, the task was completed in 30 seconds.
Microsegmentation projects are not always the most flashy or “sexy.” They require a fairly significant time investment, and the finished result is invisible – you can’t “see” better security, and if done well, nothing about it should impact how clients’ teams work. Tools like NSX-T, vRNI, and vRLI make the process clear, straightforward, and manageable for the clients, helping keep them focused and the project on track.
Written by Aviv Shaar, TeraSky, Cloud Native Consultant