Blog
21 April, 2024
June 20, 2022
Are you tired of searching for compatibility issues and mismatches? Search no more.
VMware has solved this issue with vSphere Lifecycle Manager.
Every one of us who is familiar with VMware vSphere environments has faced the never-ending story: patching, upgrading ESXI drivers, firmware, hotfixes, and the struggle to stay in line with VMware’s compatibility matrix.
In the past, this important task was hard to follow and consumed a lot of valuable time.
Until now, we used an external VMware tool called Update Manager (as of version 6.5, it is now embedded into the vCenter appliance). However, this great tool did not support managing the Firmware upgrade for ESXI host and the relevant adapters, so problems remained.
In vSphere 7, VMware has added a new component to the vCenter Appliance, geared to replace the Update Manager and add new, improved functionality, including Firmware upgrades. The new component is called vSphere Lifecycle Manager (vLCM).
vLCM is a new way to manage our vSphere environments, including upgrades and creating and enforcing a baseline for ESXI hosts in a given cluster.
Below is a table comparing the features of Update Manager and vLCM:
| Update Manager | vLCM |
| ESXI installation using Images | ESXI installation using Images |
| ESXI Patches | ESXI Patches |
| VMtools Upgrade | VMtools Upgrade |
| VM Hardware upgrade | VM Hardware upgrade |
| Physical Hardware Upgrade (Firmware) | |
| Managing cluster software using desired state images | |
| Verify host hardware against the VMware Compatibility Guide (VCG) and the vSAN Hardware Compatibility List (vSAN HCL). | |
| Automated Firmware Updates | |
| 1 Baseline can contain all packages needed for the entire stack |
Limitations and considerations regarding vLCM:
• All ESXI hosts must be version 7.0 and above.
• All ESXI hosts must be stateful
• All ESXI hosts must be from the same vendor.
• Cannot manage supervisor cluster.
• Cannot manage clusters that are prepared for NSX.
• If a cluster is configured to use base images, it cannot be changed back to using baselines.
• Only Dell and HPE Servers are supported for updating firmware via vLCM.
So, which tool should I use? Update manager or vLCM?
vSphere 7.0 supports both the legacy Update Manager and the new vLCM methods of managing the upgrade process. However, only one method can be used per cluster. The vSphere administrator must decide which tool is used on a per cluster basis.
When there is a desire to move to vLCM, the UI offers a “Manage with a single image” button at the root of the cluster that will begin the process of transitioning that cluster to be managed by vLCM, and not by the legacy Update Manager.
As mentioned above, not all vendors and features are supported yet with vLCM. If we have an environment with mixed server generations and vendors such that some of our servers or cluster are not supported by vLCM, we can utilize the legacy Update Manager while we can still use the advanced capabilities of vLCM where applicable. As versions progress, we will hopefully be able to migrate more and more of our environments to the new and improved vLCM. In the meantime, the choice is yours.
Explanation of basic concepts when using vLCM:
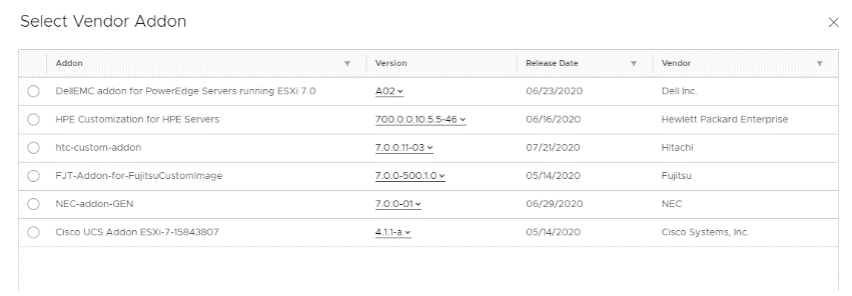
Creating an Image and attaching it to a cluster:
Using vLCM for creating an ESXI image is an easy process. In just a few simple steps, you can manage all your clusters and datacenters with one or more custom images.
When we create an image mapping to a cluster, we have two options:
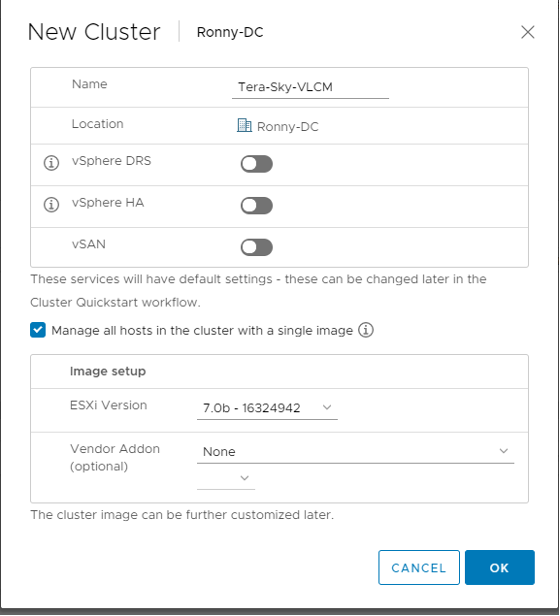
Option 1 – A New Cluster:
1) While creating the cluster, we need to enable the management of the cluster ESXI hosts using vSphere Lifecycle Manager images.
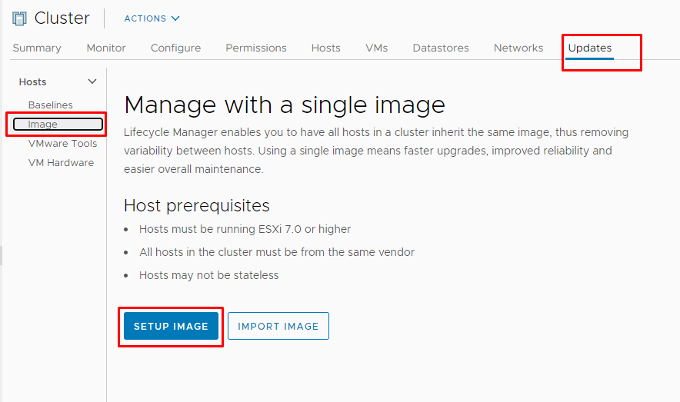
Option 2 – An Existing Cluster:
2) With existing clusters, we need to enable image management from the Updates tab for the cluster by selecting Image on the left and then clicking the Setup Image button, as shown in the image below:
Then, we will need to fill out the form with the relevant values and click Save.
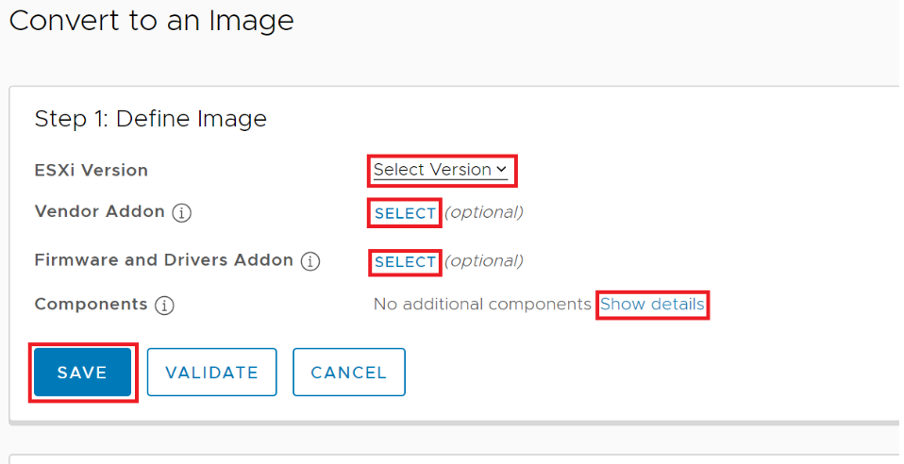
After clicking the save button, the cluster automatically performs compatibility checks.
If the cluster is not compliant with the chosen image options, vSphere Lifecycle Manager displays a list of the hosts that are non-compliant and lists the issues with each host.
Step 2:
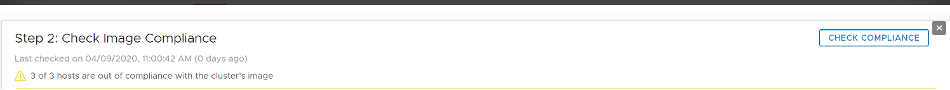
In Step 2, we have the option to validate our image and check the compliance against our ESXI hosts. After clicking the Finish button, The vCenter will create a notification to inform us that it will replace all existing and attached baselines from the cluster with the one we just created.
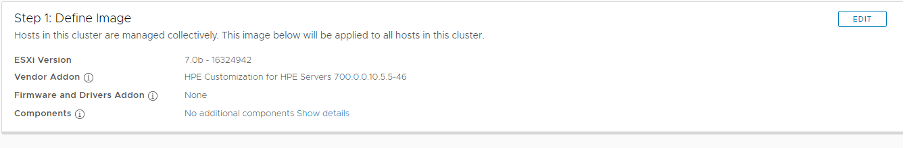
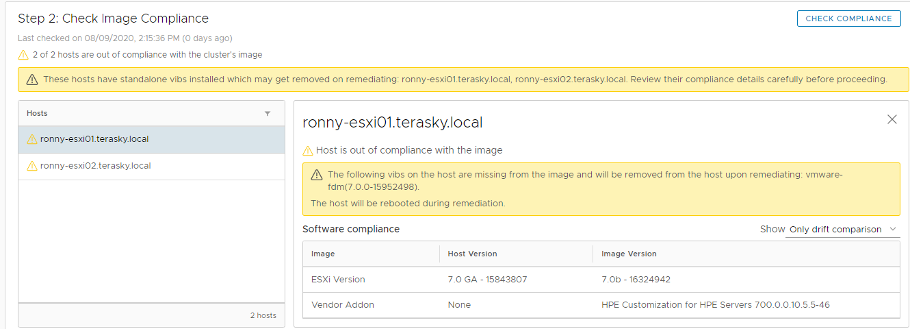
Double Check for the Finish Setup process:
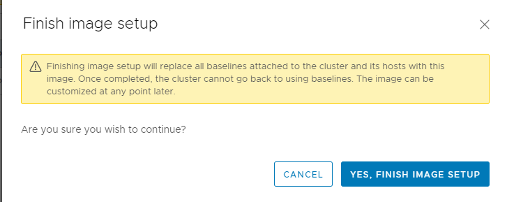
Checking host hardware against the vendor compatibility list in the VMware HCL
One of the major improvements vLCM offers is the ability to check hardware firmware and verify if the host is in line with the VMware Compatibility Guide.
To perform this check, we click on the 3 dots located in the top right corner of vLCM.
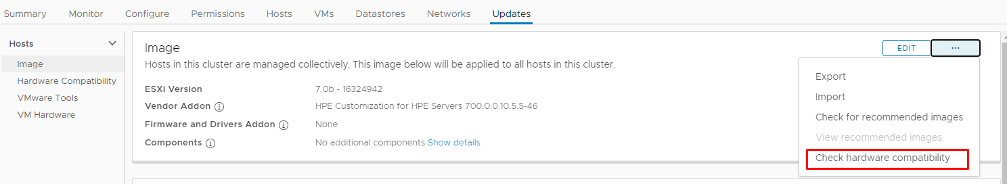
After clicking on “Check hardware compatibility,” the checks will run automatically against the VMware HCL. When the checks are complete, we will be informed if we are currently in a supported configuration. If we are not in a supported configuration, a notification provides details about what exactly needs to be upgraded for the specific hardware we are using.
Troubleshooting:
In the event of any issues with the vLCM, we can find multiple new logs regarding all aspects of the vLCM components at the following path on the vCenter appliance:
/var/log/vmware/vLCM
Conclusion
vLCM has brought to the table amazing new capabilities, including the ability to manage our required firmware and the hardware vendor and third-party packages we need in our environment.
vLCM provides the ability to have one image per cluster that is constantly validated against the HCL to make sure we are always in a supported configuration, making the environment easier to manage overall.
No more non-compliant states between ESXI and clusters.
No more misconfiguration.
No more time is wasted on upgrading each component separately.
This is a major update for us vSphere Administrators who are always trying to keep our environments up to date with the best practices and highest supported versions.
I am excited to see how this tool will progress and gain more functionality in the coming releases!
Written by: Adiel Gilboa, Hybrid Cloud & Automation Solutions Architect